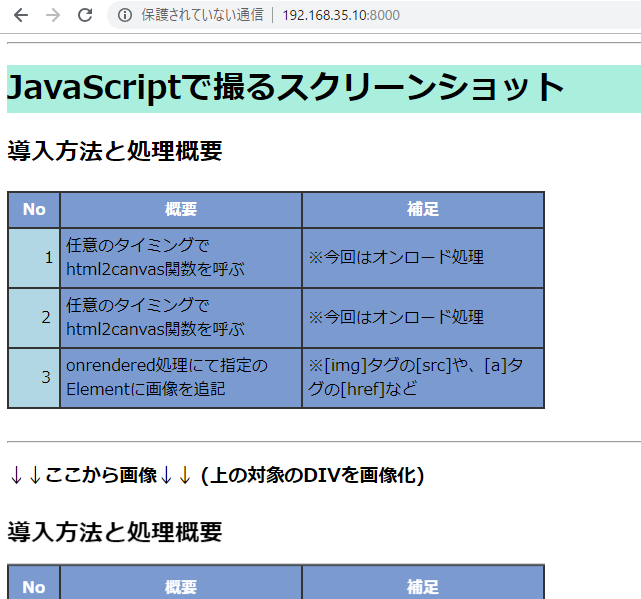
CHARACTER_OCTET_LENGTH must be the same as CHARACTER_MAXIMUM_LENGTH except for multibyte character set.
mysql> select * from `information_schema`.`columns` where `table_schema` = “test”;
+—————+————–+————+————-+——————+—————-+————-+———–+————————–+————————+——————-+—————+——————–+——————–+—————–+————–+————+—————-+———————————+—————-+
| TABLE_CATALOG | TABLE_SCHEMA | TABLE_NAME | COLUMN_NAME | ORDINAL_POSITION | COLUMN_DEFAULT | IS_NULLABLE | DATA_TYPE | CHARACTER_MAXIMUM_LENGTH | CHARACTER_OCTET_LENGTH | NUMERIC_PRECISION | NUMERIC_SCALE | DATETIME_PRECISION | CHARACTER_SET_NAME | COLLATION_NAME | COLUMN_TYPE | COLUMN_KEY | EXTRA | PRIVILEGES | COLUMN_COMMENT |
+—————+————–+————+————-+——————+—————-+————-+———–+————————–+————————+——————-+—————+——————–+——————–+—————–+————–+————+—————-+———————————+—————-+
| def | test | items | item_id | 1 | NULL | NO | int | NULL | NULL | 10 | 0 | NULL | NULL | NULL | int(11) | PRI | auto_increment | select,insert,update,references | |
| def | test | items | name | 2 | NULL | YES | text | 65535 | 65535 | NULL | NULL | NULL | utf8 | utf8_general_ci | text | | | select,insert,update,references | |
| def | test | items | price | 3 | NULL | YES | int | NULL | NULL | 10 | 0 | NULL | NULL | NULL | int(11) | | | select,insert,update,references | |
| def | test | name | name | 1 | NULL | YES | varchar | 255 | 765 | NULL | NULL | NULL | utf8 | utf8_general_ci | varchar(255) | | | select,insert,update,references | |
| def | test | name | password | 2 | NULL | YES | varchar | 255 | 765 | NULL | NULL | NULL | utf8 | utf8_general_ci | varchar(255) | | | select,insert,update,references | |
| def | test | news | id | 1 | NULL | NO | int | NULL | NULL | 10 | 0 | NULL | NULL | NULL | int(11) | PRI | auto_increment | select,insert,update,references | |
| def | test | news | content | 2 | NULL | YES | varchar | 100 | 300 | NULL | NULL | NULL | utf8 | utf8_general_ci | varchar(100) | | | select,insert,update,references | |
| def | test | user | id | 1 | NULL | NO | int | NULL | NULL | 10 | 0 | NULL | NULL | NULL | int(11) | MUL | auto_increment | select,insert,update,references | |
| def | test | user | name | 2 | NULL | YES | varchar | 20 | 60 | NULL | NULL | NULL | utf8 | utf8_general_ci | varchar(20) | | | select,insert,update,references | |
+—————+————–+————+————-+——————+—————-+————-+———–+————————–+————————+——————-+—————+——————–+——————–+—————–+————–+————+—————-+———————————+—————-+
9 rows in set (0.15 sec)
なんじゃーこりゃーーー