configure:os,cupやバージョンを調べたり、関連ツールを調査
make ソースコードをコンパイル
make install は既定のディレクトリにコピー
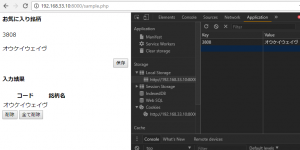
localstorageのkeyを調べ、一致したらvalueを表示
正規表現で、keyの先頭に”38″がついていた場合には、pタグでlocalstorageのvalueを表示しています。
window.onload = function(){
var list = document.getElementById(“list”)
for (var i =0; i < localStorage.length; i++){
var p = document.createElement("p");
list.appendChild(p);
var str = localStorage.key(i);
if ( str.match(/^38/)){
p.innerHTML = localStorage.getItem(str);
}
}
}
[/php]
pタグの中身をlocalstorageに保存するには
getElementById に、innerHTMLを付ければOKですね。
var key = document.getElementById("myid").innerHTML;
var value = document.getElementById("myid2").innerHTML;
if (key && value){
storage.setItem(key, value);
}
key = "";
value = "";
<?php
$code = array('3808','8893');
$name = array('オウケイウェイヴ','新日本建物');
?>
<h4>お気に入り銘柄</h4>
<p id = "code"><?php echo $code[0]; ?></p>
<p id = "name"><?php echo $name[0]; ?></p>
local storage にkey valueを保存
<script type="text/javascript">
if(typeof localStorage == 'undefined'){
document.write("<p>お使いのブラウザではお気に入り機能が使えません。</p>");
} else {
var storage = localStorage;
function setlocalStorage(){
var key = document.getElementById("textkey").value;
var value = document.getElementById("textdata").value;
if (key && value){
storage.setItem(key, value);
}
key = "";
value = "";
viewStorage();
}
function removeStorage(){
var key = document.getElementById("textkey").value;
storage.removeItem(key);
key = "";
viewStorage();
}
function removeallStorage(){
storage.clear();
viewStorage();
}
function viewStorage() {
var list = document.getElementById("list")
while(list.firstChild)list.removeChild(list.firstChild);
for (var i=0; i < storage.length; i++){
var _key = storage.key(i);
var tr = document.createElement("tr");
var td1 = document.createElement("td");
var td2 = document.createElement("td");
list.appendChild(tr);
tr.appendChild(td1);
tr.appendChild(td2);
td1.innerHTML = _key;
td2.innerHTML = storage.getItem(_key);
}
}
function load(){
var list = document.getElementById("list")
while (list.firstChild) list.removeChild(list.firstChild);
for (var i =0; i < localStorage.length; i++){
var _key = localStorage.key(i);
var tr = document.createElement("tr");
var td1 = document.createElement("td");
var td2 = document.createElement("td");
list.appendChild(tr);
tr.appendChild(td1);
tr.appendChild(td2);
td1.innerHTML = _key;
td2.innerHTML = localStorage.getItem(_key);
}
}
}
</script>
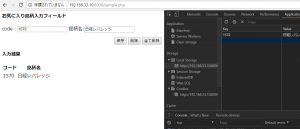
<h4>お気に入り銘柄入力フィールド</h4>
<p> code : <input id="textkey" type="text"/> 銘柄名:<input id="textdata" type="text"/></p>
<p align="right"><button id="button" onclick="setlocalStorage()">保存</button>
<button id="button" onclick="removeStorage()">削除</button>
<button id="button" onclick="removeallStorage()">全て削除</button></p>
<h4>入力結果</h4>
<table class="tagForList2">
<tr>
<th>コード</th><th>銘柄名</th>
</tr>
<tbody id="list">
</tbody>
</table>
コンテンツの表示非表示 – javascript
bodyでonloadしてdisplay = “none”とすると、処理に時間がかかった場合、onloadが終わるまで表示されるので、bodyのonloadよりも綺麗に見えますね。
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
<title>表示</title>
</head>
<body>
<a href="#" onclick="btn1_click()">今日の運勢を見る</a><br>
<p id="p1">大吉</p>
<script>
document.getElementById("p1").style.display = "none";
function btn1_click(){
var y1 = document.getElementById("p1");
if(y1.style.display=="block"){
y1.style.display ="none";
}else{
y1.style.display ="block";
}
}
</script>
</body>
</html>
グローバルスコープとローカルスコープ
globalでロカールスコープの変数をグローバルでも使えるようにします。
<?php
function sell($name){
$code = "8411";
echo $name."さんは" .$code."を空売りしています。";
}
sell('Barclays Bank');
echo $code. "は、出来高の多い銘柄です。"
?>
Barclays Bankさんは8411を空売りしています。は、出来高の多い銘柄です。
globalで宣言します。
<?php
function sell($name){
global $code;
$code = "8411";
echo $name."さんは" .$code."を空売りしています。";
}
sell('Barclays Bank');
echo $code. "は、出来高の多い銘柄です。"
?>
Barclays Bankさんは8411を空売りしています。8411は、出来高の多い銘柄です。
多次元配列の定義
下層をつくるには、更にarray()でくくってあげればOKですね。
<?php $stock= array( '0' => array ( 'code' => '4578', 'name' => 'ラクオリア創薬', 'price' => '5550', 'pts' => array ( 'pprice' => '5550', 'volume' => '100', ) ), '1' => array ( 'code' => '3825', 'name' => 'リミックスポイント', 'price' => '892', 'pts' => array ( 'pprice' => '911', 'volume' => '40400' ) ) ); var_dump($stock); ?>
array(2) { [0]=> array(4) { [“code”]=> string(4) “4578” [“name”]=> string(21) “ラクオリア創薬” [“price”]=> string(4) “5550” [“pts”]=> array(2) { [“pprice”]=> string(4) “5550” [“volume”]=> string(3) “100” } } [1]=> array(4) { [“code”]=> string(4) “3825” [“name”]=> string(27) “リミックスポイント” [“price”]=> string(3) “892” [“pts”]=> array(2) { [“pprice”]=> string(3) “911” [“volume”]=> string(5) “40400” } } }
cURL関数:curl_init
外部のサイトにアクセスして、さまざまな情報を取ってきたい場合の関数
リクエスト方法のカスタマイズが、file_get_contentsより自由
//初期化 $ch = curl_init(); //headerを表示するか curl_setopt($curl, CURLOPT_HEADER, 0); //レスポンスを表示するか curl_setopt($curl, CURLOPT_RETURNTRANSFER, 0); //cookieを指定 curl_setopt($curl, CURLOPT_COOKIEJAR, $cookie); //postで送信 curl_setopt($curl, CURLOPT_POST, 1); ?>
<?php $url = "https://www.mercari.com/jp/search/?keyword=%E5%84%AA%E5%BE%85"; $ch = curl_init(); curl_setopt($ch, CURLOPT_URL, $url); curl_setopt($ch, CURLOPT_HEADER, 0); $html = curl_exec($ch); var_dump($html); curl_close($ch); ?>
Error 403 Forbidden
error_reporting = E_ALL
関係者全員にメールする、だと思ってましたが、「全てのエラーを表示する」でした。
error_reporting = E_ALL
紛らわしい。
simplexml_load_stringの使い方 2
<h3>xml</h3>
<?php
$axmlData = array();
$axmlData[0] = array
(
"name"=> "楽天日本株4.3倍ブル",
"rate" => "123.54",
"asset" => "27625"
);
$axmlData[1] = array
(
"name" => "小型株ファンド",
"rate" => "107.11",
"asset" => "24381"
);
$sStringXML = '<?xml version="1.0" encoding="UTF-8"?>'."\n";
echo $axmlData[0][rate];
$sStringXML .= "<list>"."\n";
foreach($axmlData as $value){
$sStringXML .= "<item>";
$sStringXML.= "<return>".$value['rate']."</return>";
$sStringXML .= "<toshin>".$value['name']."</toshin>";
$sStringXML .= "<shisan>".$value['asset']."</shisan>";
$sStringXML .= "</item>"."\n";
}
$sStringXML .= "</list>"."\n";
echo '[PHP ruler="true" toolbar="true"]'.htmlentities($sStringXML, ENT_QUOTES, 'UTF-8').'<\/pre>';
echo "<br>";
$xml = simplexml_load_string($sStringXML);
foreach($xml->item as $value){
$name = $value->toshin;
$return = $value->return;
$asset = $value->shisan;
echo 'name:'.$name.'<br/>';
echo 'return:'.$return.'<br/>';
echo 'asset:'.$asset.'<br>';
}
?>
name:楽天日本株4.3倍ブル
return:123.54
asset:27625
name:小型株ファンド
return:107.11
asset:24381
つまり、下記のxml:return, toshin, shisanを切り取ってくれるということですね。
<?xml version="1.0" encoding="UTF-8"?> <list> <item><return>123.54</return><toshin>楽天日本株4.3倍ブル</toshin><shisan>27625</shisan></item> <item><return>107.11</return><toshin>小型株ファンド</toshin><shisan>24381</shisan></item> </list>
