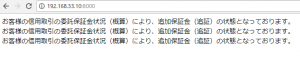
API Client Libraries offers simple, flexible, powerful access to many Google APIs.
Setup
1. sign up Google account
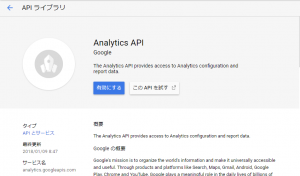
2. create a project in the Google API Console
3. Install the library
google-api-php-client
https://github.com/google/google-api-php-client
Authentication and authorization
All API calls must use either simple or authorized access.
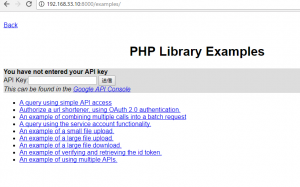
API Key: to authenticate your application, use API Key for your Google API Console.
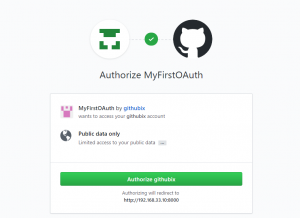
Authorized API access(OAuth 2.0)
your application must be authenticated, the user must grant access for your application, and the user must be authenticated in order to grant that access.
scope: each api defines one or more scopes that declare a set of operations permitted.
Refresh and access tokens: when a user grants your application access, the OAuth 2.0 authorization server provides your application with refresh and access tokens.
Client ID and client secret: these strings uniquely identify your application and are used to acquire tokens.
Build the client object
$client = new Google_Client();
$client->setApplicationName("My Application")
$client->setDeveloperKey("My_SIMPLE_API_KEY")
Build the service object
services are called through queries to service specific objects. These are created by constructing the service object, and passing an instance of Google_Client to it.
$service = new Google_Service_Books($client);
Calling an API
each API provides resources and methods, usually in chain. These can be accessed from the service object in the form $service->resource->method(args). Most method require some arguments, then accept a final parameter of an array containing optional parameters.
$optParams = array('filter' => 'free-ebooks');
$results = $service->volumes->listVolumes('Henry David Thoeau', $optParams);
Handling the result
There are two main types of response – items and collections of items. Each can be accessed either as an object or as an array.
foreach($results as $item){
echo $item['volumeInfo']['title'], "<br />\n";
}