震度センサー
圧力・気圧センサー
電流センサー
雨量・水位センサー
風量センサー
マイクロホン
人感センサー
開閉センサー
CCD/CMOSイメージセンサー
二酸化炭素センサー
GPS
電子コンパス
湿度・温度センサー
ジャイロセンサー
照度センサー
機械学習の利用用途
識別
情報の判別・仕分け・検索
音声、画像、動画の意味理解
異常検知・予知
予測
数値予測
ニーズ・意図予測
マッチング
実行
表現生成
デザイン
行動の最適化
行動の自動化
音声AI 「科大讯飞」(iFLYTEK)
・時価総額:1.5兆
・中国AIシェア:95%
・翻訳機国内利用者:5億人以上
これヤベーな。
GPUメーカー
大手GPUメーカー
– Nvidia
– Intel
– AMD
まずNvidia
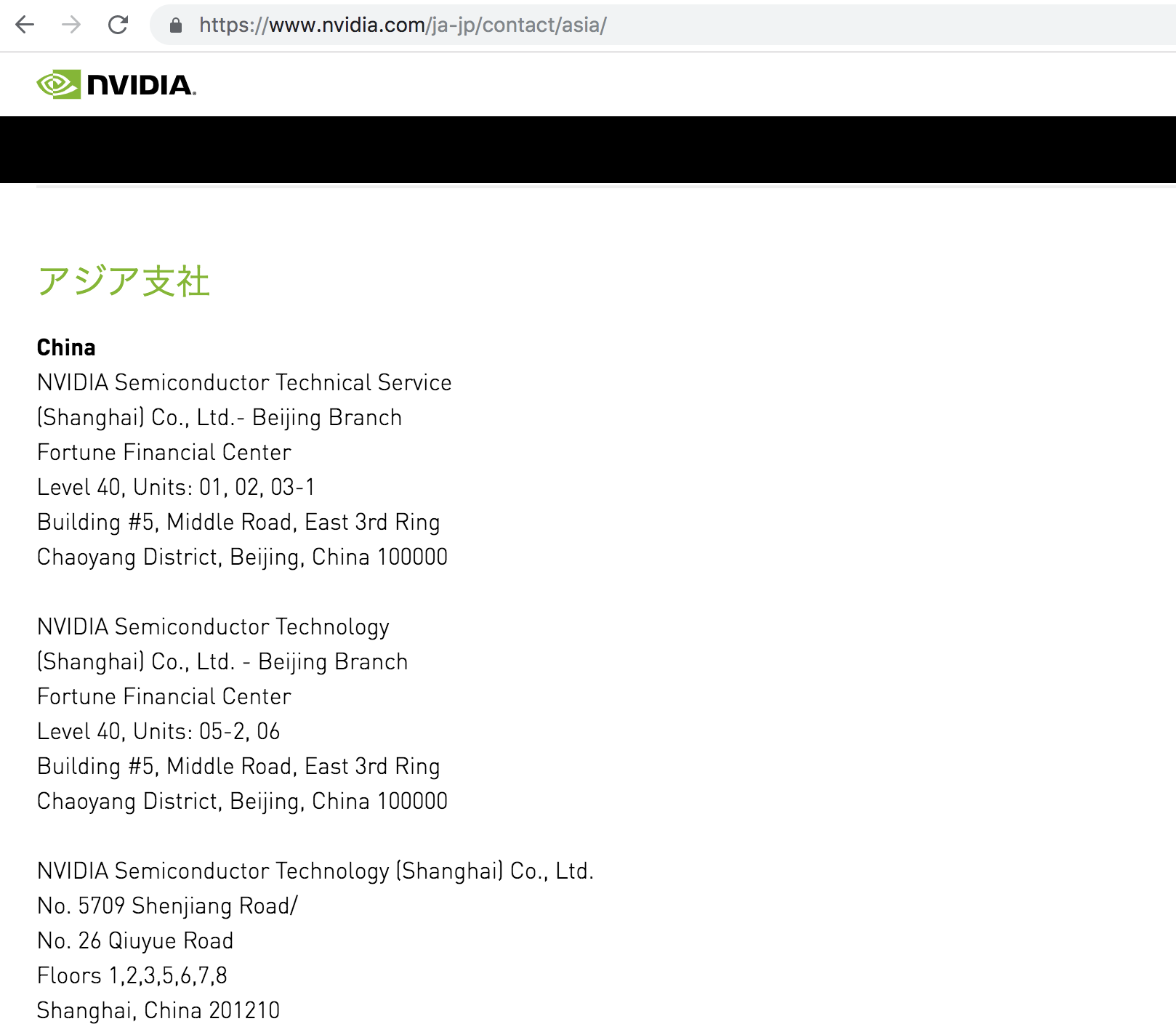
やべーなこれ、日本は全く相手にされてないな。
What we need to see:
BS or MS in Computer Science or equivalent program from an accredited University / College
10+ years of hands-on experiences building software and/or scalable cloud services
Strong self-initiative, passion, interpersonal skills, and agility working with new technology
Hands-on development of high quality distributed system features and/or cloud scale services, and RESTful web services
Experience with cloud system infrastructure, cloud-scale software, Continuous Integration and Continuous Delivery (CI/CD)
Demonstrated skills in wide variety of languages including: Java and Python
Deep understanding of cloud design in the areas of virtualization and global infrastructure, distributed systems, load balancing and security
Track record of crafting well-designed solutions and delivering high-quality software on time
Intel
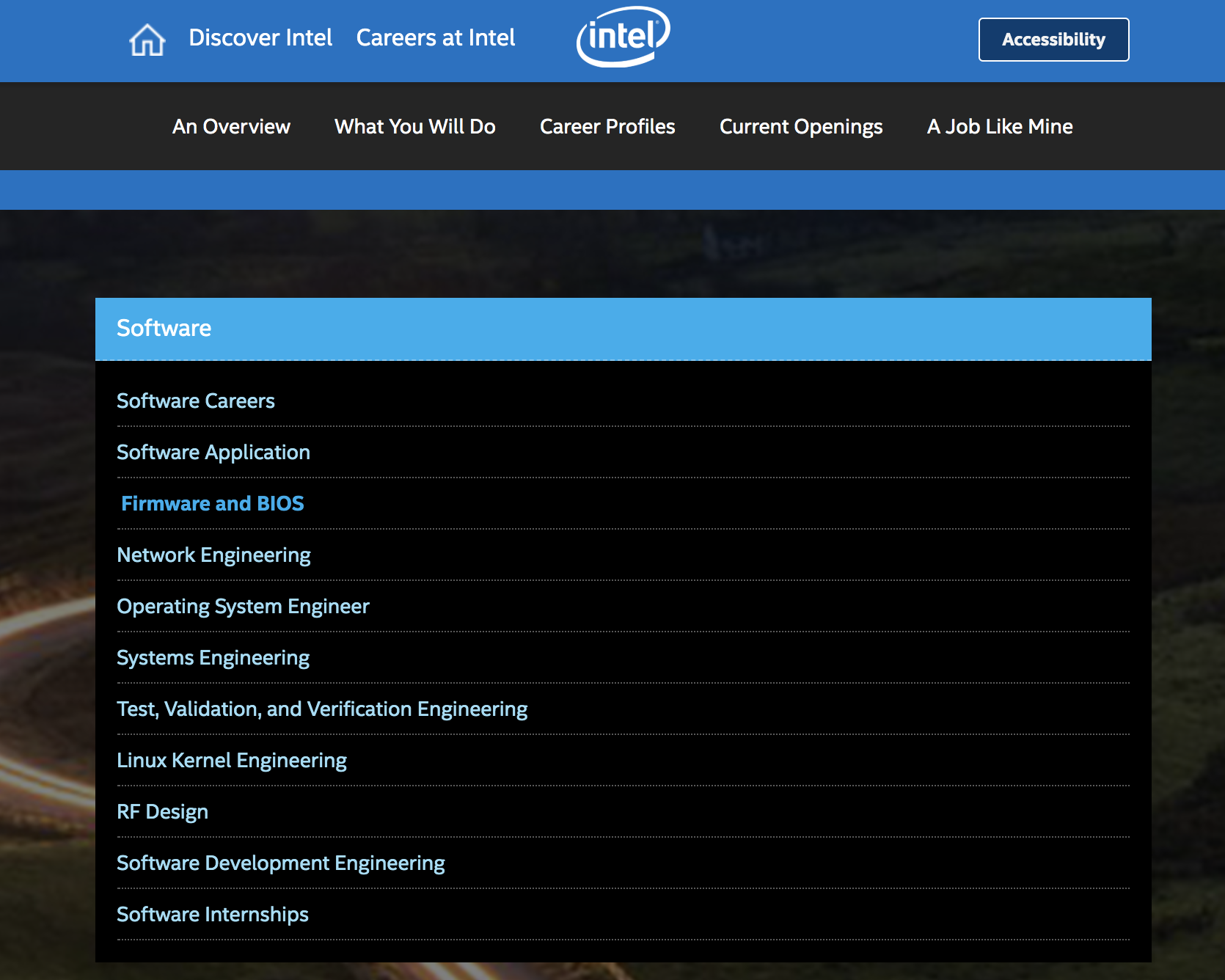
AMD
REQUIREMENTS:
Advanced programming skills in C for operating system kernel & systems development
Experience with the GNU toolchain
Proficient use of git
Experience building and submitting patches on a mailing list and in general collaborative open source development
Excellent understanding of operating systems concepts, data structures, the x86-64 architecture, and virtualization
Experience with low level debug tools as well as emulators and simulators
Experience with open source software development
Experience working with external software partners
Experience running, analyzing, and tuning system performance benchmarks
Strong analysis and problem solving skills
Proven interpersonal skills, technical and team leadership and collaboration
Excellent written and verbal communication skills
Programming skills with Python and Bash
Preferred experience with Jenkins for CI/CT.
やべーなこれ。。
Azureのmachine learning
Microsoftの機械学習はどんな感じでしょうか?
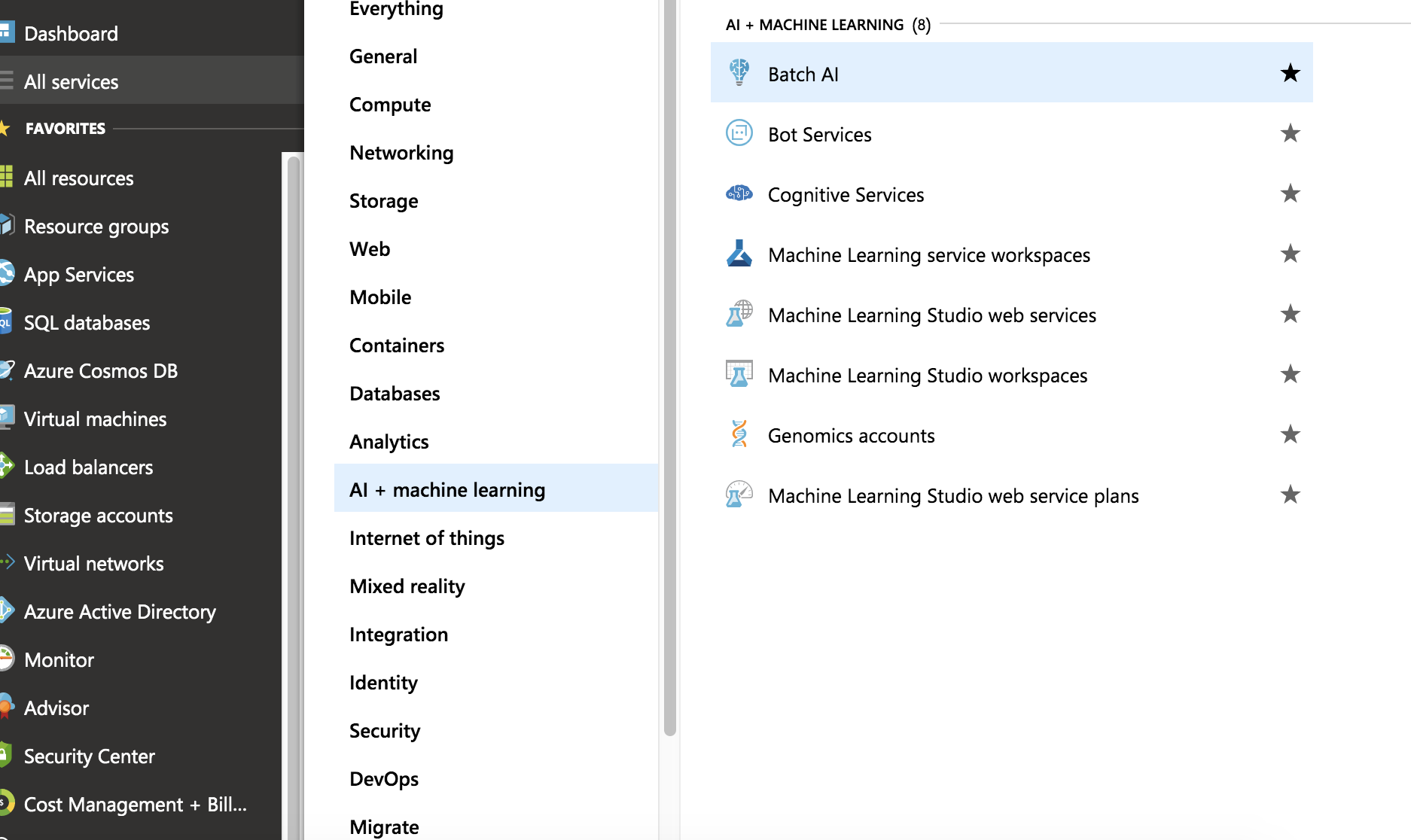
– Bach AI
– Bot Service
– Cognitive Services
– Machine Learning service workspaces
– Machine Learning Studio web services
– Machine Learning Studio workspaces
– Genomics accounts
– Machine Learning Studio web service plan
Machine Learning Studio web services
必要なデータ、フィルタ、計算モデル等のロジックをドラック&ドロップで配置する
ん、ちょっと待てよ
Mean Absolute Error
Root Mean Squared Error
Relative Absolute Error
Relative Squared Error
Coefficient of Determination
これは別に機械学習でもなんでもないように思うんだが。。
GCPの機械学習サービス
どんなものがあるか見てみましょう
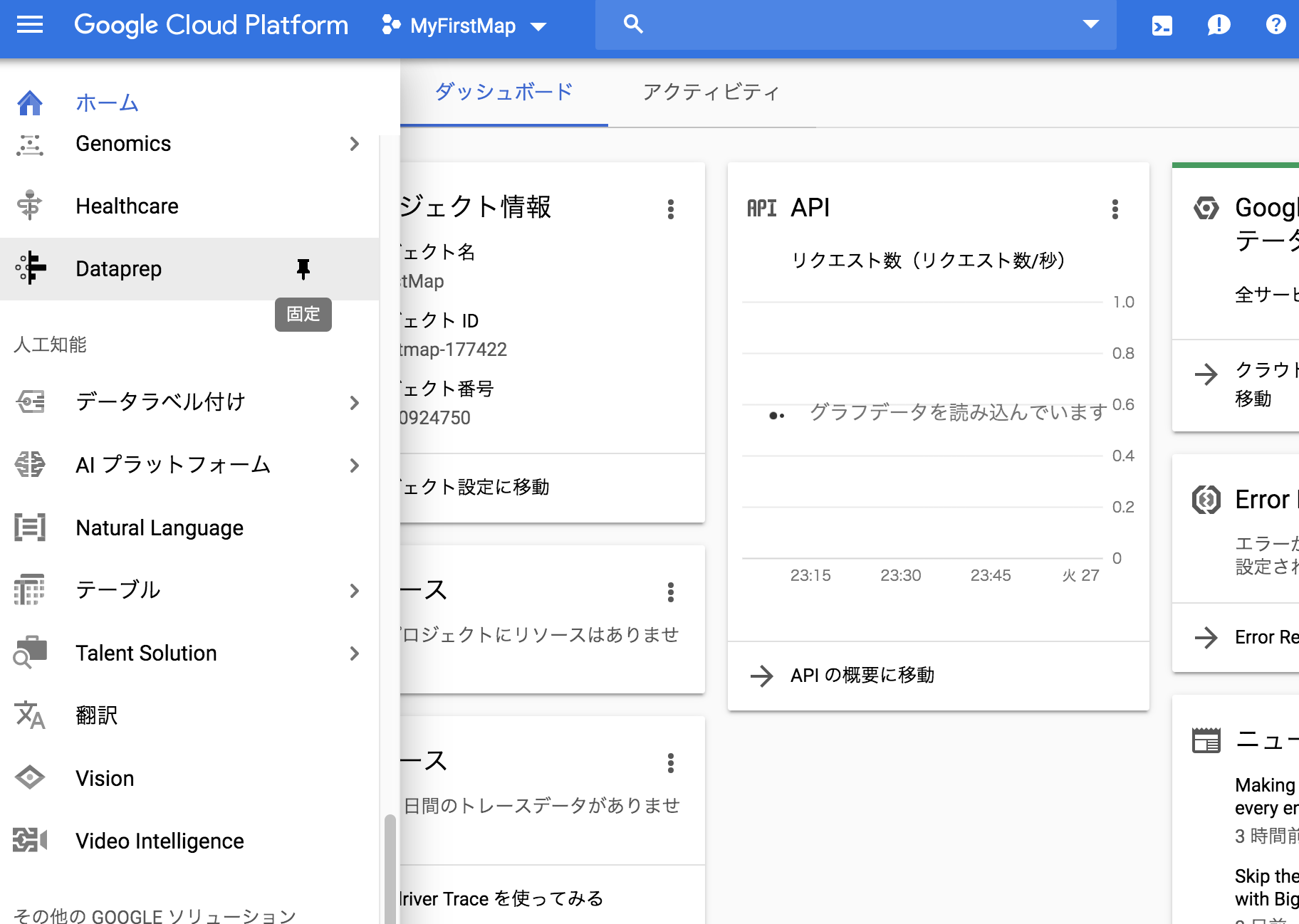
データラベル付け
AIプラットフォーム
Natural Language
テーブル
Talent Solution
翻訳
Vision
Video Intelligence
うーん、tutorialでもGCPだと金がかかりそうだなー
その前に、tensor flowを理解しろ、って言ってるな。
https://cloud.google.com/ml-engine/docs/tensorflow/getting-started-training-prediction
なんかやること多すぎないか。。
AWSの機械学習サービス
ざっと見ただけでも色々ありそうだ
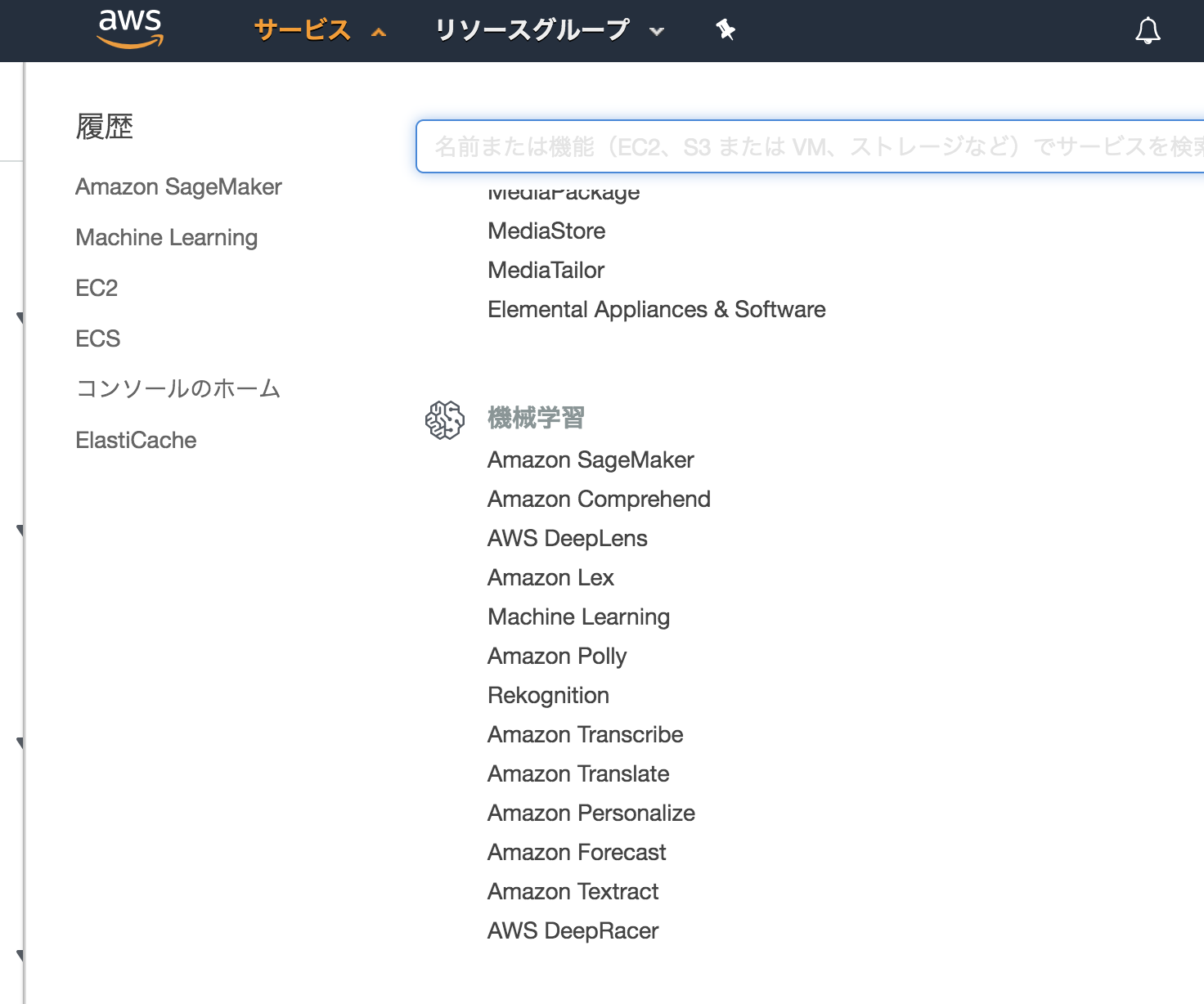
Amazon SageMaker:データサイエンティスト、機械学習エンジニア向け
Amazon Comprehend:自然言語処理
AWS DeepLens
Amazon Lex:会話型インターフェイス、チャットボット
Machine Learning:線形回帰、ロジスティック回帰、多項ロジスティック回帰
Amazon Polly:テキストを音声変換
Rekognition:画像や動画を用意するだけで検出
Amazon Transcribe:文字起こしサービス
Amazon Translate
Amazon Personalize:パーソナライズ、レコメンデーション
Amazon Forecast:時系列予想
Amazon Textract:書類からテキストの抽出
AWS DeepRacer:自律走行
1.予測のみ行うサービス:Transcribe, Polly
2.ユーザーは学習データのみ用意し、サービス側でモデルをトレーニング:Comprehend, Machine Learning
3.インフラを気にせずモデルのトレーニング/評価/デプロイ:SageMaker
1と2は機械学習の知識がなくても利用できる。3はインフラ管理が減る。
つまり、AWSで機械学習サービスをやるならsageMakerってところか。。
amazon recognitionはサービスへの導入が比較的イメージしやすいかも。使ってみたい。
Laravelでseederを使おう
まず、seeder fileを作ります。
[vagrant@localhost test]$ php artisan make:seeder SmartTableSeeder
Seeder created successfully.
すると、database/seeds配下に SmartTableSeeder.php が出来る。
runメソッドでデータ挿入
use Illuminate\Database\Seeder;
class SmartTableSeeder extends Seeder
{
/**
* Run the database seeds.
*
* @return void
*/
public function run()
{
$ministers = ['taro', 'masatoshi', 'takashi','masahiko','takumi'];
foreach ($ministers as $minister) {
DB::table('minister')->('minister')
}
}
}
あれ、DB::table(‘minister’)->(‘minister’) って、なんかおかしいぞ。
で、シーダーファイルは、DatabaseSeeder.phpから呼び出す。
use Illuminate\Database\Seeder;
class DatabaseSeeder extends Seeder
{
/**
* Run the database seeds.
*
* @return void
*/
public function run()
{
// $this->call(UsersTableSeeder::class);
$this->call('SmartTableSeeder::class');
}
}
seeder 実行
[vagrant@localhost test]$ php artisan db:seed
Seeding: SmartTableSeeder::class
In Container.php line 729:
Class SmartTableSeeder::class does not exist
ん?
[vagrant@localhost test]$ php composer.phar dump-autoload
Generating optimized autoload filesCarbon 1 is deprecated, see how to migrate to Carbon 2.
https://carbon.nesbot.com/docs/#api-carbon-2
You can run ‘./vendor/bin/upgrade-carbon’ to get help in updating carbon and other frameworks and libraries that depend on it.
Generated optimized autoload files containing 3116 classes
[vagrant@localhost test]$ php artisan db:seed
Seeding: SmartTableSeeder::class
In Container.php line 729:
Class SmartTableSeeder::class does not exist
あれええええええー
あ、こうか
use Illuminate\Database\Seeder;
class DatabaseSeeder extends Seeder
{
/**
* Run the database seeds.
*
* @return void
*/
public function run()
{
// $this->call(UsersTableSeeder::class);
$this->call(
SmartTableSeeder::class
);
}
}
[vagrant@localhost test]$ php artisan db:seed
Seeding: SmartTableSeeder
In Connection.php line 647:
SQLSTATE[42S02]: Base table or view not found: 1146 Table ‘test.minister’ d
oesn’t exist (SQL: insert into `minister` (`age`, `name`) values (54, taro)
, (54, taro))
In Connection.php line 445:
SQLSTATE[42S02]: Base table or view not found: 1146 Table ‘test.minister’ d
oesn’t exist
うん、seederが複数あるときと、一つの場合だと書き方が異なりますね。
migrationしてないので、カラムが無いと表示されていますが、seederについてはわかりました。
AWS AMI
AMIは”Amazon Machine Image”の略。
AMIはインスタンスのルートボリュームのテンプレートが含まれ、インスタンスの丸ごとバックアップが取れる。
EC2のイメージの作成からAMIを作成する
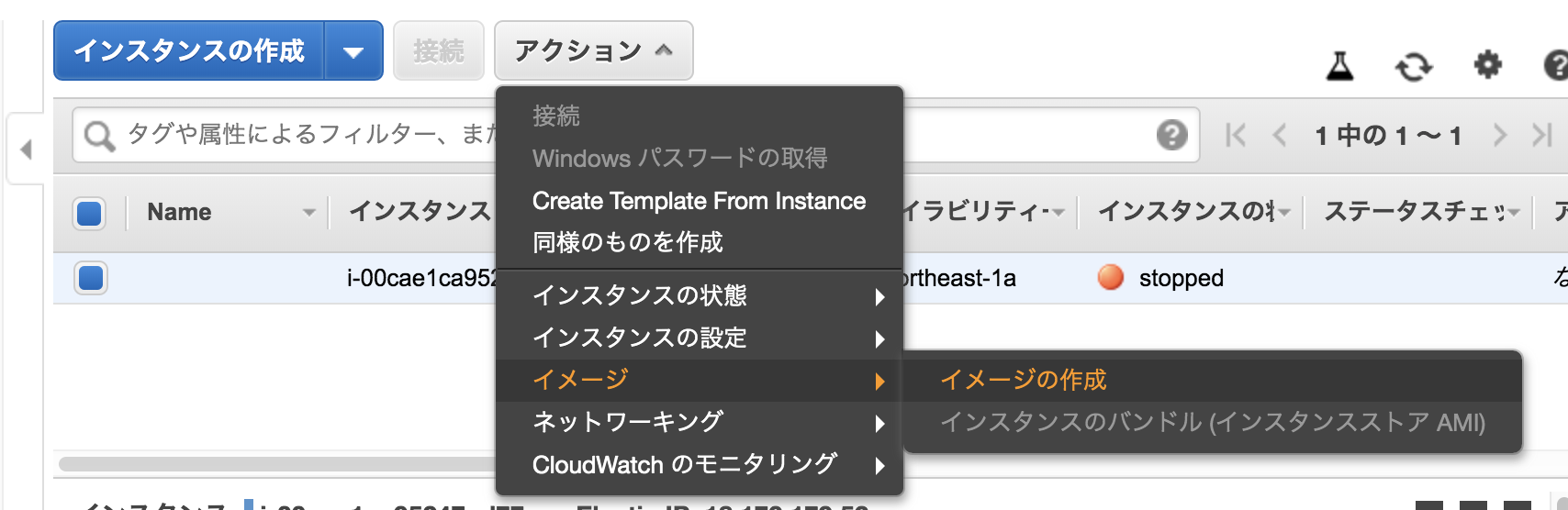
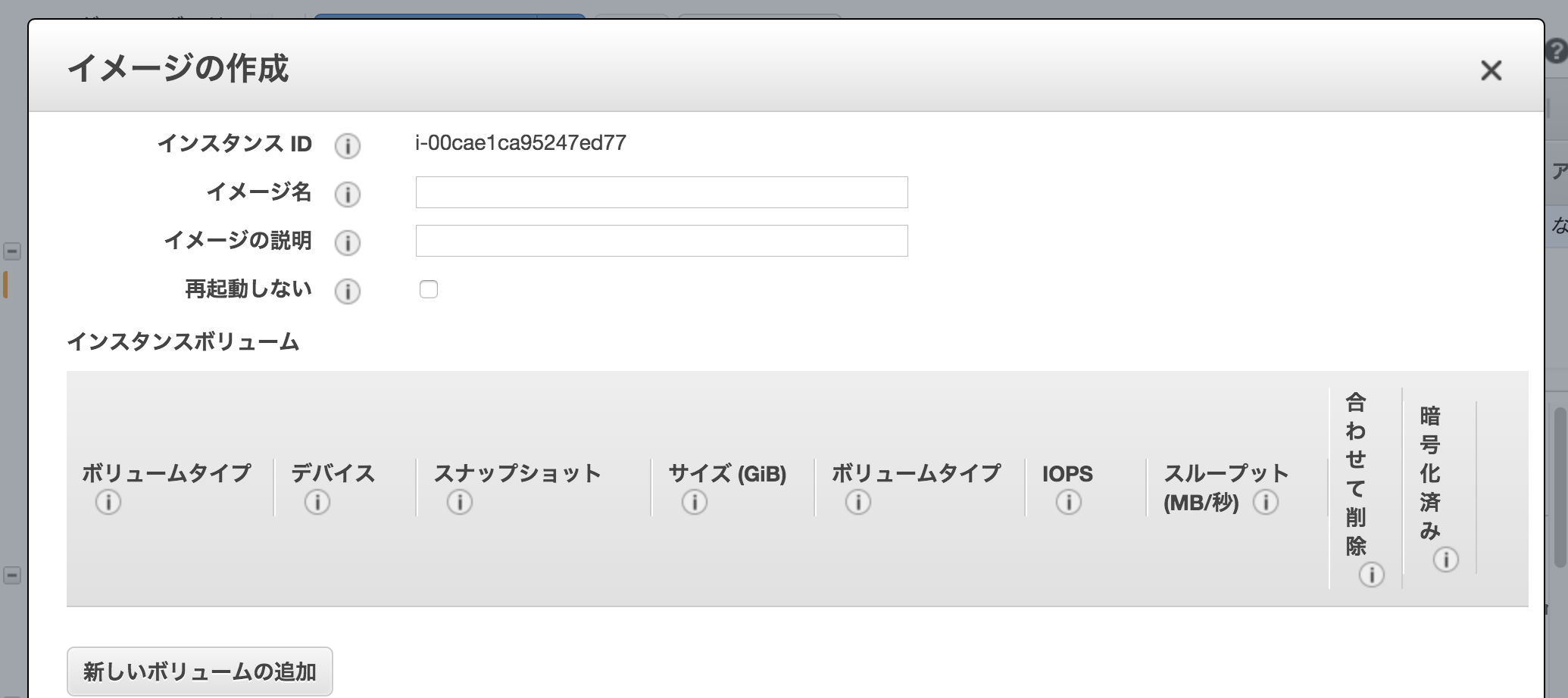
AMIをローンチすると、EC2が立ち上がる。
なるほど、これは凄い便利ですねー
Amazon Elastic Container Service(ECS)って何?
何やらECSを知ってないと駄目らしい。
ECSって何?英会話教室? あ、それECCね。
ECSはAmazon Elastic Container Serviceの略。
クラスターでDockerコンテナを簡単に実行、停止、管理できるコンテナ管理サービス。
あれ、Dockerのデプロイならk8sじゃなかったっけ??
まず公式から。
https://docs.aws.amazon.com/ja_jp/AmazonECS/latest/developerguide/Welcome.html
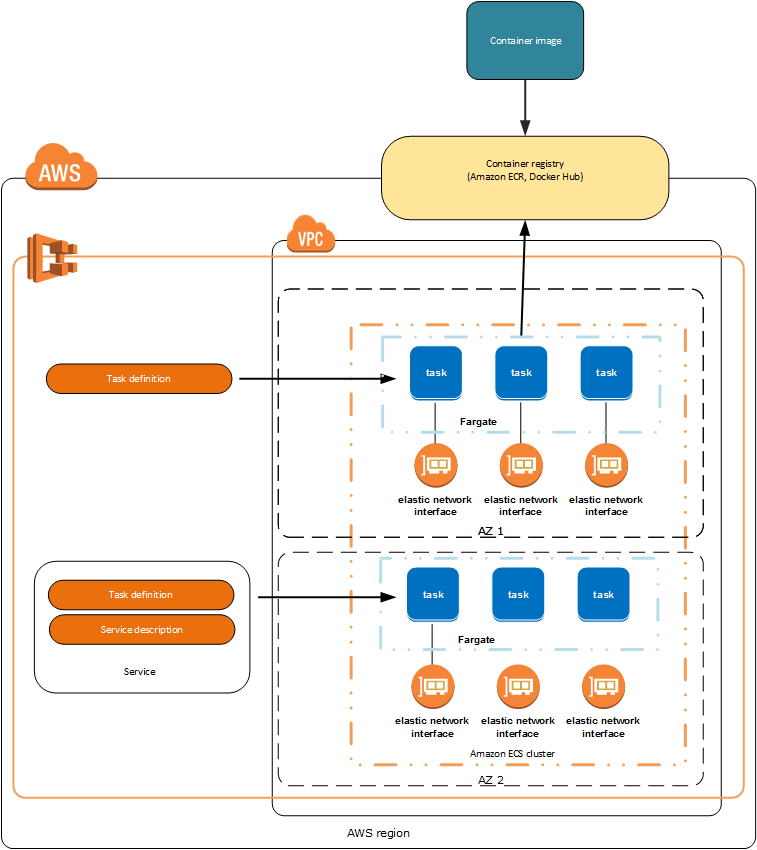
ロードバランサのポートマッピングやコンテナの生死監視、自動復旧などをやってくれるのね。
やってるのは、ecs-agentというのをコンテナとして起動して、confにcluster名を渡してあげているだけとのこと。
autoscaling groupを使ってインスタンスを立てて、その起動スクリプトでacs-agentを動かす。
ecsのクラスターの作成
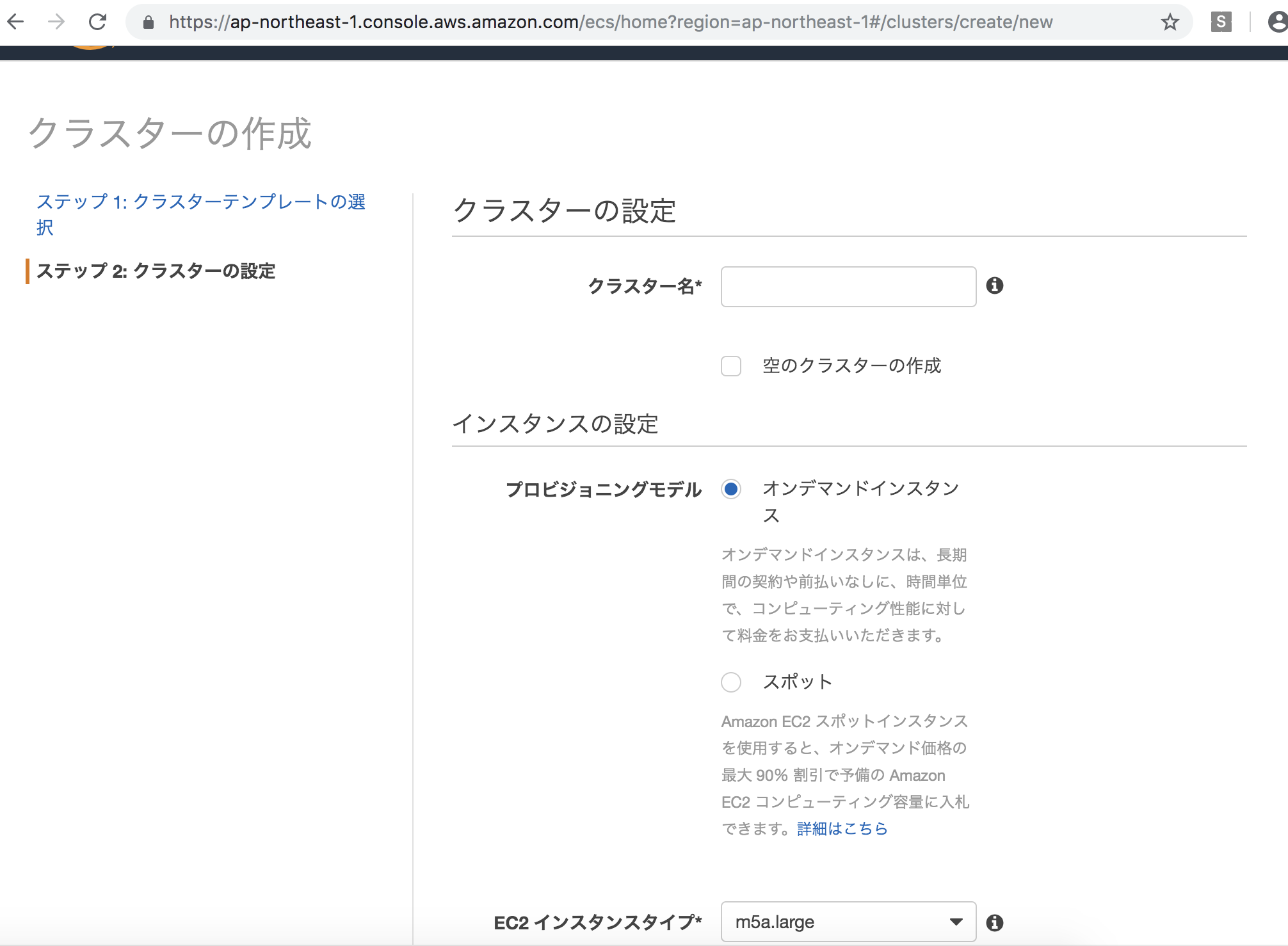
まあ、dockerでサービスやるなら、ってところか。
