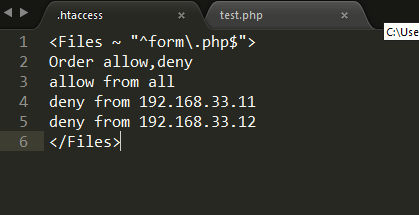
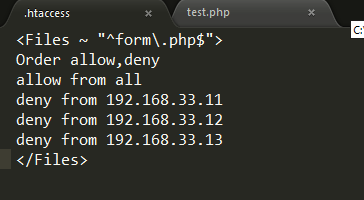
On demand self service
Broad or wide network access
Resource pooling or sharing
Measured service
Rapid elasticity
SaaS, PaaS, IaaS
Software as a servicd: use the provider’s applications running on a cloud infrastructure
Platform as a service: consumer-created applications using programming languages and tools supported by the provider
Infrastructure as a service: Capability provided to the consumer to provision processing, storage, networks, and other fundamental computing resources
Key Issues:
Trust, multi-tenancy, encryption, compliance
Clouds are massively complex systems
Simple primitives and common functional units
Cloud security challenges
– trusting vendor’s security model
– Customer inability to respond to audit findings
– Obtaining support for investigations
– Indirect administrator accountability
– Proprietary implementations can’t be examined
– Loss of physical control
Primary Technology
-Virtualization
-Grid technology
-Service Oriented Architectures
-Distributed Computing
-Broadband Networks
Hypervisor has higher privilege than guest kernel
Security VM is separated from User VM
User = application + data (encrypt)
Frequency Analysis Attack
connect data with public information
Optimization Attack