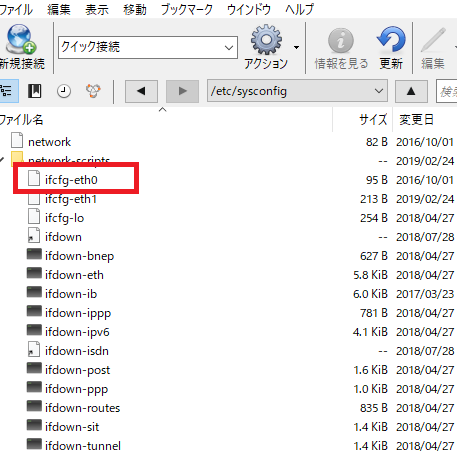
iptablesとは一般的なLinuxに搭載されているパケットフィルタ
パケットとは、ネットワーク上を流れるデータの事。パケットフィルタとは、このパケットを選別して、通すものと通さないものを分けるということを意味
iptablesは商用製品に匹敵する、とても高機能かつ高性能なパケットフィルタ
サーバ自身を守ることはもちろん、パケット転送などにも対応しているため、ネットワークアダプタを二つ搭載したマシンの上で動作させパケット転送制御を行うことで、ネットワーク型ファイアウォールとしても使用可能
現在設定されているポリシー
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all — anywhere anywhere ctstate RELATED,EST ABLISHED
ACCEPT all — anywhere anywhere
INPUT_direct all — anywhere anywhere
INPUT_ZONES_SOURCE all — anywhere anywhere
INPUT_ZONES all — anywhere anywhere
DROP all — anywhere anywhere ctstate INVALID
REJECT all — anywhere anywhere reject-with icmp-ho st-prohibited
Chain FORWARD (policy ACCEPT)
target prot opt source destination
ACCEPT all — anywhere anywhere ctstate RELATED,EST ABLISHED
ACCEPT all — anywhere anywhere
FORWARD_direct all — anywhere anywhere
FORWARD_IN_ZONES_SOURCE all — anywhere anywhere
FORWARD_IN_ZONES all — anywhere anywhere
FORWARD_OUT_ZONES_SOURCE all — anywhere anywhere
FORWARD_OUT_ZONES all — anywhere anywhere
DROP all — anywhere anywhere ctstate INVALID
REJECT all — anywhere anywhere reject-with icmp-ho st-prohibited
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
OUTPUT_direct all — anywhere anywhere
Chain FORWARD_IN_ZONES (1 references)
target prot opt source destination
FWDI_public all — anywhere anywhere [goto]
FWDI_public all — anywhere anywhere [goto]
Chain FORWARD_IN_ZONES_SOURCE (1 references)
target prot opt source destination
Chain FORWARD_OUT_ZONES (1 references)
target prot opt source destination
FWDO_public all — anywhere anywhere [goto]
FWDO_public all — anywhere anywhere [goto]
Chain FORWARD_OUT_ZONES_SOURCE (1 references)
target prot opt source destination
Chain FORWARD_direct (1 references)
target prot opt source destination
Chain FWDI_public (2 references)
target prot opt source destination
FWDI_public_log all — anywhere anywhere
FWDI_public_deny all — anywhere anywhere
FWDI_public_allow all — anywhere anywhere
ACCEPT icmp — anywhere anywhere
Chain FWDI_public_allow (1 references)
target prot opt source destination
Chain FWDI_public_deny (1 references)
target prot opt source destination
Chain FWDI_public_log (1 references)
target prot opt source destination
Chain FWDO_public (2 references)
target prot opt source destination
FWDO_public_log all — anywhere anywhere
FWDO_public_deny all — anywhere anywhere
FWDO_public_allow all — anywhere anywhere
Chain FWDO_public_allow (1 references)
target prot opt source destination
Chain FWDO_public_deny (1 references)
target prot opt source destination
Chain FWDO_public_log (1 references)
target prot opt source destination
Chain INPUT_ZONES (1 references)
target prot opt source destination
IN_public all — anywhere anywhere [goto]
IN_public all — anywhere anywhere [goto]
Chain INPUT_ZONES_SOURCE (1 references)
target prot opt source destination
Chain INPUT_direct (1 references)
target prot opt source destination
Chain IN_public (2 references)
target prot opt source destination
IN_public_log all — anywhere anywhere
IN_public_deny all — anywhere anywhere
IN_public_allow all — anywhere anywhere
ACCEPT icmp — anywhere anywhere
Chain IN_public_allow (1 references)
target prot opt source destination
ACCEPT tcp — anywhere anywhere tcp dpt:ssh ctstate NEW
Chain IN_public_deny (1 references)
target prot opt source destination
Chain IN_public_log (1 references)
target prot opt source destination
Chain OUTPUT_direct (1 references)
target prot opt source destination
chain forward, chain inputなどがある
Chain INPUT (policy DROP)
Chain FORWARD (policy DROP)
Chain OUTPUT (policy ACCEPT)
ルーティングして、input, forward, outputしてアプリケーションに接続している。
あああああああああ、これやべーやつだ。