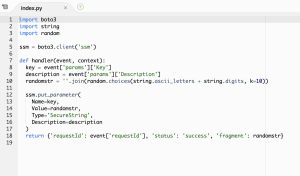
AWS Systems Manager (SSM) セッションマネージャーを使用して実行中のコンテナとの接続を確立する
Linux コンテナでのみサポート
-> fargateでは特定のバージョン(1.4.0)以降を使うと、SSMをインストールする必要がない
CloudFormationのpropertiesで、EnableExecuteCommand: trueと書く
EcsExecRolePolicy:
Type: AWS::IAM::Policy
Properties:
PolicyName: Ecs-exec-role
PolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Action:
- "ssmmesages:CreateControlChannel"
- "ssmmesages:CreateDataChannel"
- "ssmmesages:OpenControlChannel"
- "ssmmesages:OpenDataChannel"
Resource: "*"
Roles:
Service:
Type: AWS::ECS::Service
Properties:
Cluster: !Ref Cluster
DeploymentConfiguration:
MaximumPercent: 200
MinimumHealthyPercent: 100
DesiredCount: !Ref DesiredCount
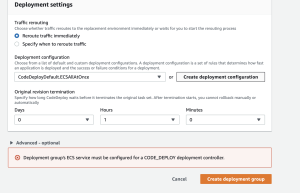
EnableExecuteCommand: true
LaunchType: FARGATE
LoadBalancers:
- ContainerName: app
ContainerPort: 80
TargetGroupArn: arn
NetworkConfiguration:
AwsvpcConfiguration:
AssignPublicIp: ENABLED
SecurityGroups:
- arn
Subnets:
- arn
- arn
ServiceName: SampleFargate
TaskDefinition: !RefTaskDefinition
なるほど、OKそうには見える