<?php
function paging($limit,$page,$disp=5){
$page = empty($_GET["page"])? 1: $_GET["page"];
$next = $page + 1;
$prev = $page - 1;
if($page != 1){
print '<a href="?page=' .$prev. '">« 前へ</a>';
}
if($page < $limit){
print '<a href="?page='.$next.'">次へ »</a>';
}
}
$limit = 10;
$page = empty($_GET["page"])? 1:$_GET["page"];
?>
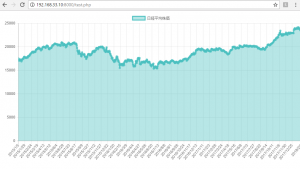
csvデータからPHP・chart.jsで、日経平均株価のチャートを作ってみた
簡単すぎるぞ~
<?php
$data = file('nikkei225.csv', FILE_IGNORE_NEW_LINES);
unset($data[0],$data[-1]);
function cut($item){
return explode(',', $item);
}
$data = array_map("cut", $data);
foreach ($data as $value){
$days[] = $value[0];
$high[] = $value[3];
$low[] = $value[4];
}
/*
$php_day = json_encode($days);
$php_json = json_encode($low);*/
?>
<html>
<head>
<script src="https://cdnjs.cloudflare.com/ajax/libs/Chart.js/2.1.4/Chart.min.js"></script>
</head>
<body>
<p><?php echo $php_json; ?></p>
<canvas id="stage"></canvas>
</body>
<script type="text/javascript">
var array = <?php echo json_encode($days, JSON_HEX_TAG | JSON_HEX_AMP | JSON_HEX_APOS | JSON_HEX_QUOT); ?>;
console.log(array);
var array2 = <?php echo json_encode($high, JSON_HEX_TAG | JSON_HEX_AMP | JSON_HEX_APOS | JSON_HEX_QUOT); ?>;
console.log(array2);
var ctx = document.getElementById("stage");
var myLineChart = new Chart(ctx, {
//グラフの種類
type: 'line',
//データの設定
data: {
//データ項目のラベル
labels: array,
//データセット
datasets: [{
//凡例
label: "日経平均株価",
//背景色
backgroundColor: "rgba(75,192,192,0.4)",
//枠線の色
borderColor: "rgba(75,192,192,1)",
//グラフのデータ
data: array2
}]
},
//オプションの設定
options: {
scales: {
//縦軸の設定
yAxes: [{
ticks: {
//最小値を0にする
beginAtZero: true
}
}]
}
}
});
</script>
</html>
トレーダー関数
“;
foreach ($atrs as $idx => $atr){
$price = $data[idx];
$highest = max($highest, $price[2]);
$losscutLine = round($highest – $atr * ATR_N, 2);
echo implode(“,”,[
$price[0],
$highest,
$price[4],
$losscutLine,
$price[4] < $losscutLine ? '売却':'保持'
]) . "\n";
}
[/php]
phpQueryとexplode
<?php
require_once('phpquery/phpQuery/phpQuery.php');
$html = file_get_contents('');
$doc = phpQuery::newDocument($html);
$message = $doc[".message"]->text();
echo substr_count($message, '下げ');
$text = explode(" ",$message);
print_r($text);
?>

array_map()関数
array_mapは、arr1の各要素にcallback関数を適用した後、その全ての要素を含む配列を返す。
所得税の累進課税でみてみましょう。
<?php
function tax($income){
if($income < 195){
return $income *0.05;
} elseif ($income < 330){
return $income * 0.1 + 9.75;
} elseif ($income< 695) {
return $income * 0.2 + 42.75;
} elseif ($income < 900) {
return $income * 0.23 + 63.6;
} elseif ($income < 1800) {
return $income * 0.33 + 153.6;
} elseif ($income < 4000) {
return $income * 0.40 + 279.6;
} else {
return $income * 0.45 + 479.6;
}
}
$salary = array(603, 577, 404, 401, 661, 1126, 350, 2350, 210);
$pay = array_map("tax", $salary);
print_r($pay)
?>
Array ( [0] => 163.35 [1] => 158.15 [2] => 123.55 [3] => 122.95 [4] => 174.95 [5] => 525.18 [6] => 112.75 [7] => 1219.6 [8] => 30.75 )
配列から要素を削除
array_splice():
-配列を切り取る機能を利用して対象から値を削除する
-1つだけの値の削除や連続する値の削除に向いている
<?php
$target = array('東証1部','東証2部','東証マザーズ','JASDAQ','名証','札証','福証');
$split = array_splice($target, 4, 3);
var_dump($target);
var_dump($split);
?>
array(4) { [0]=> string(10) “東証1部” [1]=> string(10) “東証2部” [2]=> string(18) “東証マザーズ” [3]=> string(6) “JASDAQ” }
array(3) { [0]=> string(6) “名証” [1]=> string(6) “札証” [2]=> string(6) “福証” }
unset();
array_values();
配列を指定して、unsetで削除する
複数の値の削除に向いている
unsetで削除するだけで、indexは変更されない。
<?php
$target = array('東証1部','東証2部','東証マザーズ','JASDAQ','名証','札証','福証');
unset($target[3]);
var_dump($target);
$target = array_values($target); //indexを詰める
var_dump($target);
?>
array(6) { [0]=> string(10) “東証1部” [1]=> string(10) “東証2部” [2]=> string(18) “東証マザーズ” [4]=> string(6) “名証” [5]=> string(6) “札証” [6]=> string(6) “福証” }
array(6) { [0]=> string(10) “東証1部” [1]=> string(10) “東証2部” [2]=> string(18) “東証マザーズ” [3]=> string(6) “名証” [4]=> string(6) “札証” [5]=> string(6) “福証” }
<?php
$portfolio = array(
'みずほフィナンシャルグループ'=> '-1.05',
'三菱UFJフィナンシャル・グループ' => '-1.35',
'野村ホールディングス' => '-2.89',
'富士通' => '-2.77',
'エー・ディー・ワークス' => '+2.27',
'日経ダブルインバース上場投信' => '+1.67',
'東芝' => '-1.54'
);
foreach ($portfolio as $key => $val){
if ($val < 0){
unset($portfolio[$key]);
}
}
array_values($portfolio);
var_dump($portfolio);
?>
array(2) { [“エー・ディー・ワークス”]=> string(5) “+2.27” [“日経ダブルインバース上場投信”]=> string(5) “+1.67” }
file()関数
file()は、ファイルの内容を取得して配列に格納する
csvファイルから直近15日の日経平均を出してみましょう。
<?php
$n = 15;
$data = file('nikkei225.csv');
rsort($data);
$i = 1;
while($i < $n+1){
echo $data[$i]."<br>\n";
$i++;
}
?>
2018/2/2,23274.53,23361.67,23367.96,23122.45
2018/2/1,23486.11,23276.1,23492.77,23211.12
2018/1/9,23849.99,23948.97,23952.61,23789.03
2018/1/5,23714.53,23643,23730.47,23520.52
2018/1/4,23506.33,23073.73,23506.33,23065.2
2018/1/31,23098.29,23205.23,23375.38,23092.85
2018/1/30,23291.97,23559.33,23581.98,23233.37
2018/1/29,23629.34,23707.14,23787.23,23580.17
2018/1/26,23631.88,23757.34,23797.96,23592.28
2018/1/25,23669.49,23750.65,23828.4,23649.03
2018/1/24,23940.78,24026.43,24072.77,23917.14
2018/1/23,24124.15,23924.4,24129.34,23916.02
2018/1/22,23816.33,23797.84,23816.33,23697.81
2018/1/19,23808.06,23854.11,23872.69,23735.61
2018/1/18,23763.37,24078.93,24084.42,23699.47
FILE_IGNORE_NEW_LINES、FILE_IGNORE_NEW_LINESなどもあります。
URL上のHTMLソースを取得することもできます。
<?php
$lines = @file('http://www.boj.or.jp/');
foreach( $lines as $line_num => $line) {
echo "{$line_num}:" . htmlspecialchars($line). "<br>/n";
}
?>
defineでリボ払い
define関数では、定数を定義することができる。
一度データとして格納すると変更できない。
サンプルとして、金利15%・毎月5000円支払いのリボ払いで購入した場合、何カ月で払い終えるか見てみましょう。
<?php
define("revolving", "5000");
class Card{
public $amount;
public $i = 0;
function revo(){
while($this->amount>0){
$this->amount = $this->amount * (0.15/12 + 1) - revolving;
$this->i++;
}
echo $this->i+1 ."<br>\n";
}
}
$gucci = new Card();
$gucci->amount = 50000;
$gucci->revo();
$chanel = new Card();
$chanel->amount = 80000;
$chanel->revo();
?>
dirname(__FILE__)
自身のいるディレクトリの絶対パスを返す。
<?php echo dirname(__FILE__); require_once(dirname(__FILE__)."/c.php"); require_once(dirname(__FILE__)."/../d.php"); ?>
サンプル
<?php require_once(dirname(__FILE__)."/vendor/autoload.php"); ?>
PHPExcel
<?php
$readFile = "20180202.xls";
$data = readXlsx($readFile);
print '<pre>';
var_dump($data);
print '</pre>';
function readXlsx($readFile)
{
require_once dirname(__FILE__) . '/PHPExcel/Classes/PHPExcel/IOFactory.php';
if(!file_exists($readFile)){
exit($readFile. "が見つかりません。");
}
$objPExcel = PHPExcel_IOFactory::load($readFile);
return $objPExcel->getActiveSheet()->toArray(null,true,true,true);
}
exit;
?>

