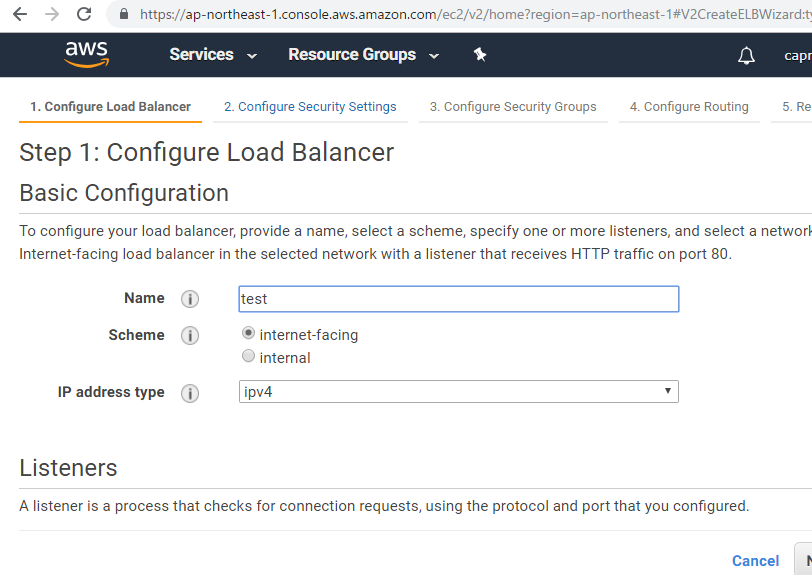
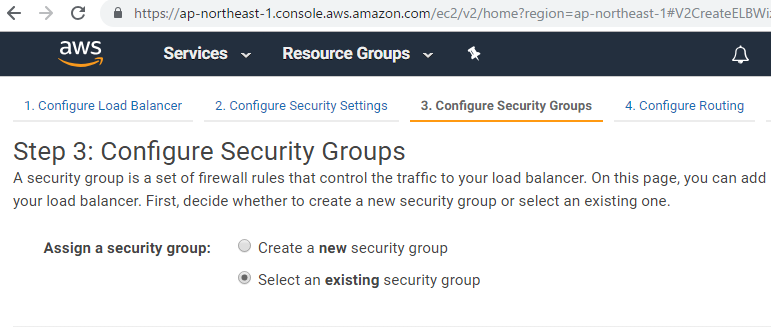
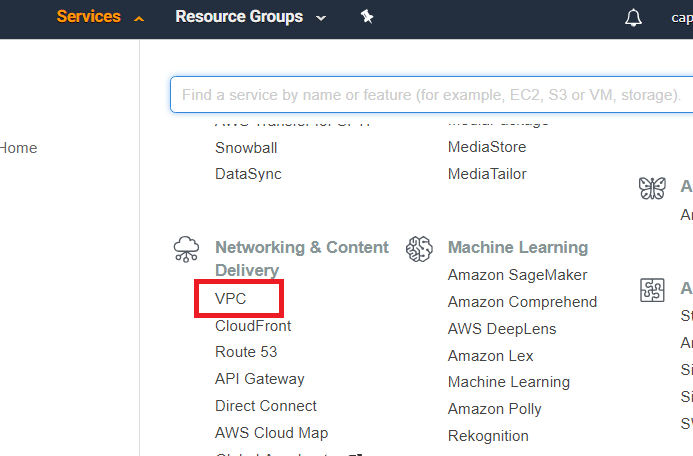
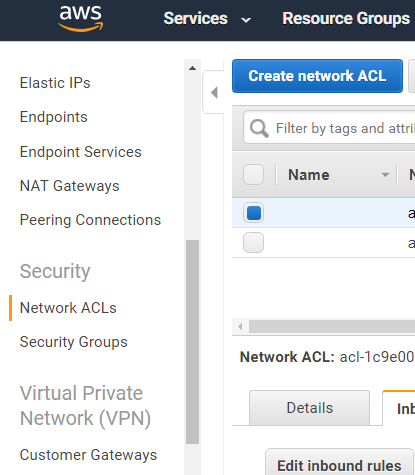
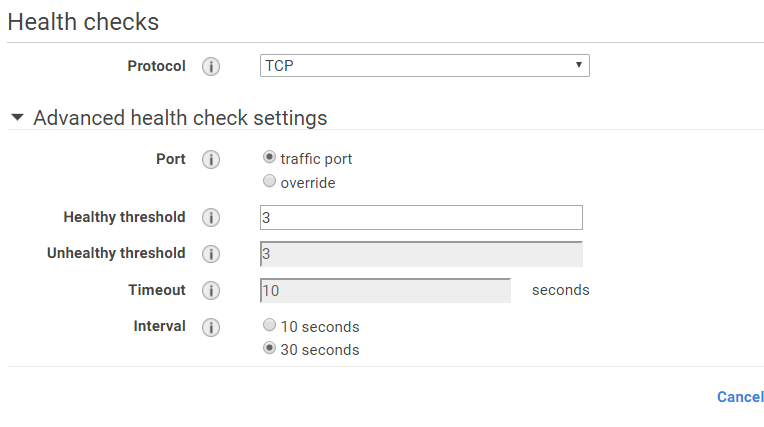
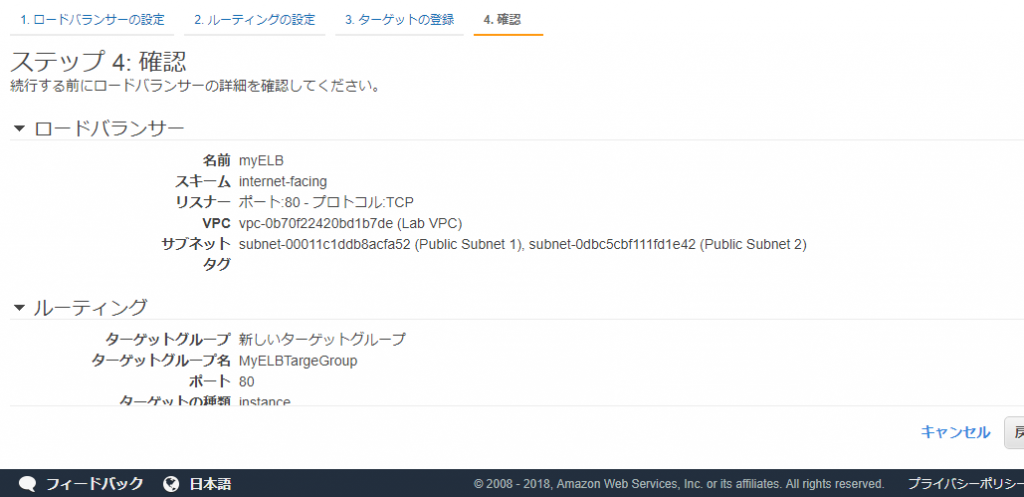
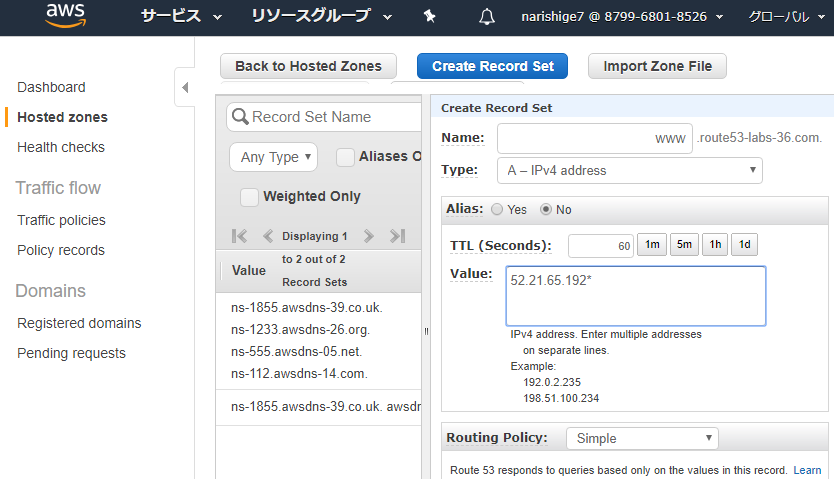
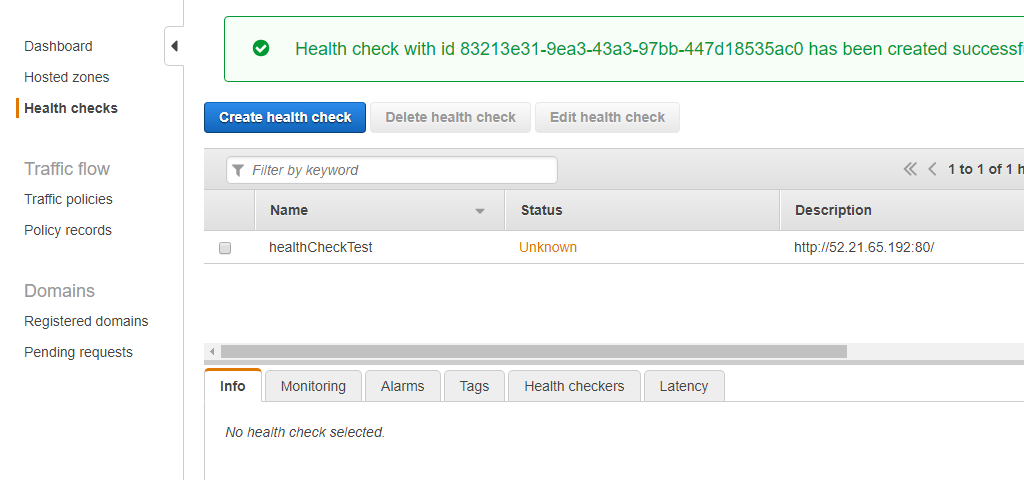
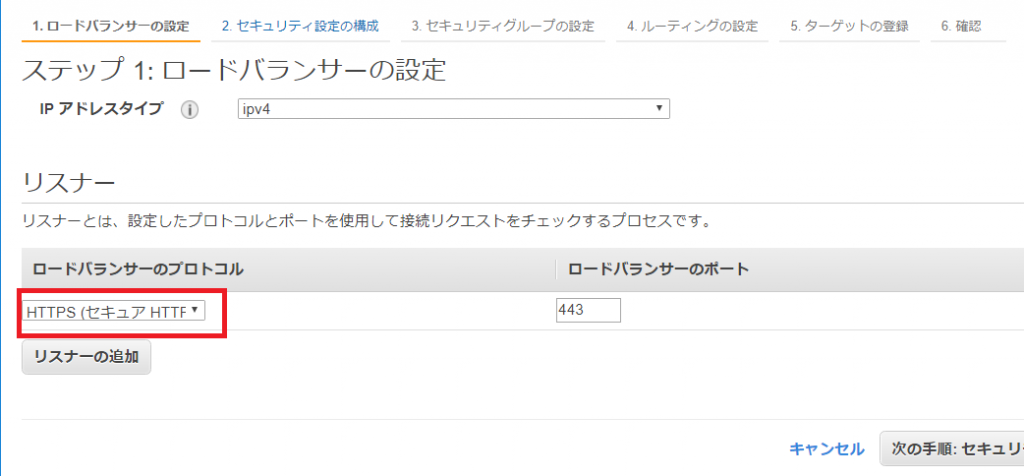
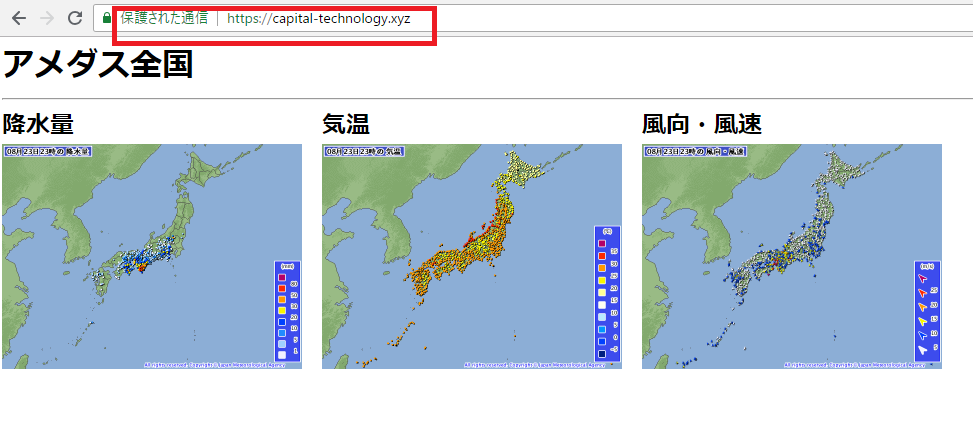
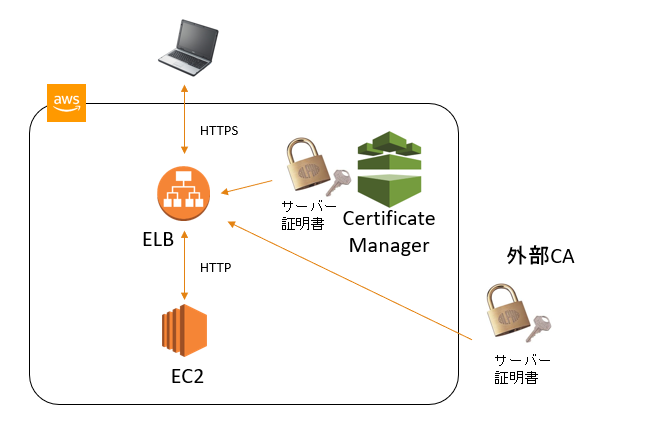
ELBでアクセスログが取得できる。
2014-03-07T07:25:38.285777Z elber 130.0.237.XX:37522 172.31.4.218:80 0.000066 0.00105 0.000037 404 404 0 570 "GET http://54.249.27.XX:80/actus4/ HTTP/1.1" 2014-03-07T07:26:43.731149Z elber 77.50.22.XXX:53477 172.31.4.218:80 0.000053 0.000866 0.000053 200 200 0 10 "GET http://54.249.27.XX:80/ HTTP/1.0" 2014-03-07T07:26:44.410747Z elber 77.50.22.XXX:53656 172.31.4.218:80 0.000052 0.000853 0.000039 404 404 0 168 "GET http://54.249.27.XX:80/foltia/ HTTP/1.0" 2014-03-07T07:26:45.084730Z elber 77.50.22.XXX:53839 172.31.4.218:80 0.000061 0.000874 0.000035 404 404 0 168 "GET http://54.249.27.XX:80/epgrec/do-record.sh HTTP/1.0" 2014-03-07T07:28:12.386207Z elber 189.206.75.XX:64289 172.31.4.218:80 0.000062 0.000924 0.000035 404 404 0 168 "GET http://54.249.27.XX:80/manager/html HTTP/1.1"
問題は、項目。
timestamp
The time accessed by the Client. UTC time, recorded in ISO 8601 format.
2014-02-15T23: 39: 43. 945958 Z
Name of ELB
ELB Name: test-loadbalancer
Client
Port Client IP address and port number
192.168.131.39.2817
Backend
port IP address and port number of the instance to which communication was distributed by ELB. This will tell you which server it was assigned to 10.0.0.0:80
request_processing_time
The time between the ELB receiving a request from the client and sending the request to the instance
0.000073
backend_processing_time
The time it takes for the ELB to send a request to an instance and the instance returns a response.
0.001048
response_processing_time
The time from when the ELB receives a response from an instance to when it returns a response to the client.
0.000057
elb_status_code
response status code.
200
backend_status_code
Response status code of the instance to which the ELB sent the request.
200
received_bytes
Size of received request (bytes)
0
sent_bytes
Size of sent request (bytes)
29
request
request from a client
“GET http://www.example.com:80/HTTP/1.1”